Vulnerability Management PowerPoint and Google Slides Template
(14 Editable Slides)
Vulnerability Management PowerPoint and Google Slides Template
Available For
Vulnerability Management is a stepwise process that deals with the identification and mitigation of vulnerabilities. While the methodology can be implemented in different domains and the organization as a whole, it is mostly related to network security. Therefore, you should train your colleagues about this crucial topic in order to strengthen your network. To start with, simply take the assistance of this professionally drafted and high-quality Vulnerability Management PowerPoint template.
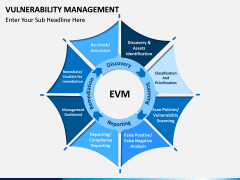
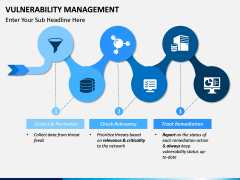
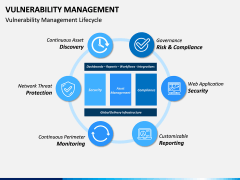
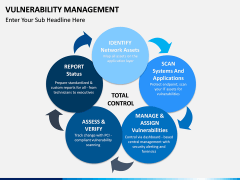
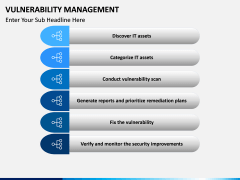
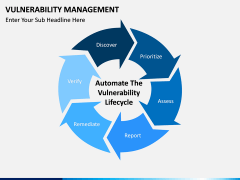
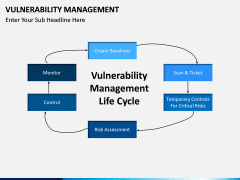
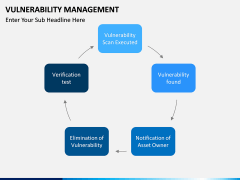
The process starts by identifying network assets. After scanning the system and the network, vulnerabilities are assigned, rectified, managed, and reported. The report status works as a feedback to make sure that a similar situation won't happen again. Now, with the help of this template, you can easily educate your audience about this topic. It is a must-have set for every professional who is related to networking and network security.
Why should you use this editable template?
- This high-definition template has been drafted by professionals after an extensive research on the topic. It will let you explain the concept in an interesting manner.
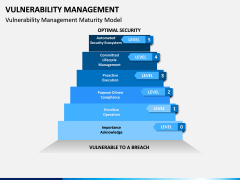
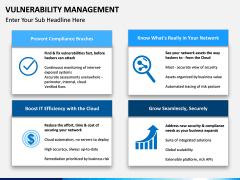
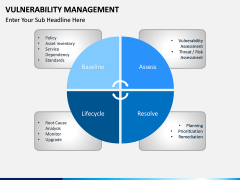
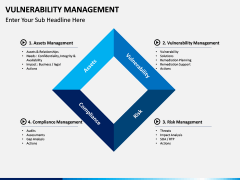
- Simply discuss the overall process and the crucial steps taken to achieve it. You can also explain its overall lifecycle, maturity model, reasons to implement it, benefits, and more.
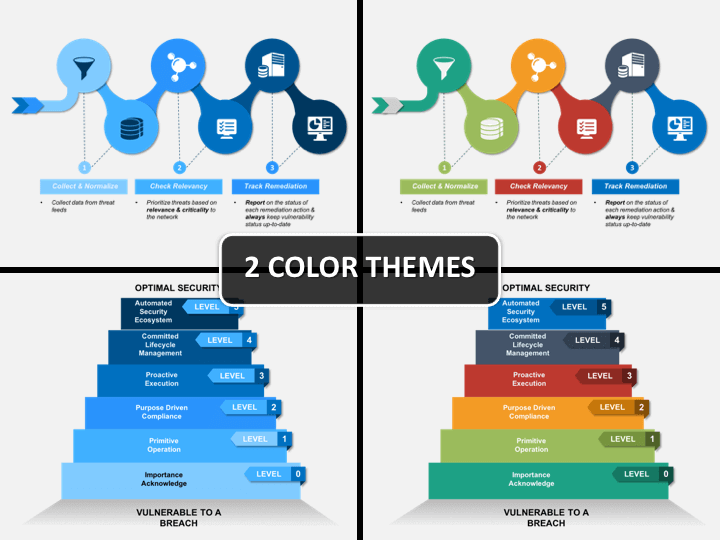
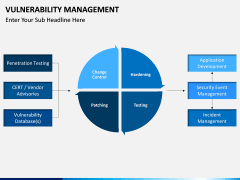
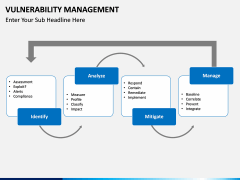
- With these illustrations, you can focus on the 4 major components of VM: Identify Analyze, Mitigate, and Manage. There are different diagrams that can help you explain these phases to your audience.
- By adding these professionally drafted visual aids to your slideshows, you can make your presentations more aesthetically pleasing. Additionally, your audience would also be able to retain the provided information.
- The template is available in different color themes and comes with a dedicated customer support.
- Based on a master slide, it is compatible with PowerPoint, Keynote, and Google Slides.
With so many advanced features, it is certainly an essential template for every professional related to network security. Even consultants and educators can use these PowerPoint slides the way they like. It is an entirely editable template and can be customized in a few minutes. This will make sure that you draft a stunning and informative presentation on the topic without spending a lot of your time and effort.